Ensuring the safety and security of the chapter house is obviously a top priority. The chapter house is not just a residence; it is a home where members build lifelong bonds, create cherished memories, and engage in activities that shape their futures. Given its significance, implementing robust security measures is essential to protect both the physical space and the well-being of its residents. One of the most advanced and effective security solutions available today is biometric entry systems.
Enhancing Security with Biometric Entry Systems
Biometric entry systems utilize unique biological traits, such as fingerprints, facial recognition, or iris scans, to grant access. Unlike traditional locks and keys or even electronic keycards, biometric systems offer several distinct advantages that make them particularly well-suited for sorority chapter houses.
- Improved Access Control: Biometric systems ensure that only authorized individuals can enter the chapter house. Unlike keys or keycards, which can be lost, stolen, or duplicated, biometric traits are unique to each person and cannot be easily replicated. This significantly reduces the risk of unauthorized access.
- Enhanced Safety: The presence of a biometric entry system can deter potential intruders and enhance the overall safety of the chapter house. Knowing that the house is equipped with advanced security technology can provide peace of mind to members, their families, and alumnae.
- Convenience and Efficiency: Biometric systems streamline the process of entering the house. Members no longer need to worry about carrying or losing keys and keycards. Access is granted swiftly and efficiently, making it easier for members to come and go while ensuring that security is never compromised,
- Accurate Tracking and Monitoring: These systems provide precise records of entry and exit times for all members. This feature is particularly useful for monitoring the house during events or identifying who was present in case of any security incidents. It also helps in managing the house occupancy efficiently.
- Durability and Low Maintenance: Biometric entry systems are typically more durable and require less maintenance compared to traditional locks. They are designed to withstand frequent use and are less susceptible to wear and tear. This longevity ensures a more reliable security solution over time.
If your chapter house utilizes a biometric security system, it is prudent to provide annual written notice to all individuals whose biometric information identifiers are collected or stored and specify the purpose of the collection and length of time the information identifiers will be held, stored, and used. Written consent and release of this information should be included in an annual housing agreement. Read more about our suggestions for Housing Agreements here.
Investing in a biometric entry system for the sorority chapter house is a forward-thinking decision that prioritizes the safety and well-being of your members. By leveraging advanced technology, the chapter can provide a secure, convenient, and efficient environment that supports the flourishing of its community. In a world where security concerns are ever-present, adopting biometric entry systems reflects a commitment to excellence and proactive care for all members of the sorority.
From May 2024 News & Notes
In times like these, the stability of your insurance companies is critical. The pandemic challenged every aspect of the fraternal community. Both your insurance companies and MJ Sorority, as your insurance agent, made significant concessions to help alleviate some of the pressures your organizations have faced.
The insurance industry went from the chaos of the pandemic to the chaos of the effects of climate change, specifically the catastrophic weather events we’ve experienced over the last several years. Insurance coverage and policy terms and conditions are on a collision course with the changing climate in many states, most notably in Florida and Louisiana. The seriousness of changing climate patterns is further compounded by the fact that in Florida’s southwestern coastline, sea levels have risen eight inches since 1950, and the risk of storm surge is estimated to double by 2030. Louisiana’s coastline is facing a similar risk. Florida is by far the most worrisome for standard property insurance companies. Several insurance companies providing property insurance in the state have gone insolvent despite state and industry efforts to prevent insolvency. To stabilize the insurance market, the Florida state government began the Florida Hurricane Catastrophe Fund in 1992. The Fund reimburses insurers for a percentage of catastrophic hurricane claims. Insurers of last resort were formed and in 2002, both carriers merged to become Citizens Property Insurance Corporation. Some additional insurance capital (or capacity) is returning to Florida in 2024, however, this has not provided much, if any, relief to consumers trying to find insured coverage for their property.
As we’ve discussed repeatedly in this newsletter, the property insurance market has been chaotic for several years. Recently, the MJ Sorority program has experienced rate increases and changes in wind and hail property deductibles in certain parts of the country.
It’s natural to feel that these changes suggest your insurance companies are abandoning the program. However, these actions are actually positioning the program for a stable future.
Without the stability of the MJ Sorority program and our partnering insurance companies, your insurance coverage would be far more vulnerable. The saying, “you get what you pay for,” is especially true for the insurance program provided by MJ Sorority. Otherwise, you risk compromising your crucial protection.
Should you wish to discuss the property insurance industry concerns further, please do not hesitate to contact us.
In the News
The property insurance crisis has been making headlines outside of your typical insurance industry publications. To learn more, we recommend the following:
- Motley Fool: How property insurance will be impacted specifically in all 50 states
- New York Times: Insurers Around the U.S. Bleed Cash From Climate Shocks
- The Daily Podcast: The Possible Collapse of the US Home Insurance System
- Fox Business: Insurance costs could surge even higher as states brace for ‘hurricane season from hell’
- Marketplace: The main reason for higher home insurance costs is climate change, which is increasing the frequency and severity of extreme weather events.
As weather patterns continue to evolve, it is crucial for housing corporations to update their chapter house roofs to withstand the increasing intensity of wind and hail events. Convective storms in particular are a major cause for concern. Convective storms are extremely severe storms with defining characteristics of high winds, sudden temperature changes, and severe thunder and lightning.
In light of these more severe weather conditions across the country, carriers are isolating geographic areas at greater risk to weather perils and are requiring additional measures be taken to update roofs. It is imperative to consider retrofitting affected chapter house roofs to mitigate risk.
Also at issue are state building codes. Many states have not updated their building codes to prepare for more severe weather, leaving existing and new structures vulnerable to sever weather damage. Building codes set the minimum standards for construction, however these standards may not always align with insurance requirements, leaving sorority houses vulnerable to potential coverage gaps. Furthermore, in many states and municipalities, building codes are not adequately enforced.
It is crucial for chapter houses in areas with inferior building codes to exceed minimum building code specifications to meet insurance expectations. This reduces the risk of roof damage and associated expenses if a convective storm hits a property. Housing corporations should be particularly wary of properties in the west and mid-west, where predictive modeling has determined a sharp increase in the frequency and severity of wind and hailstorms. Fortunately, universities are rarely near coastal areas, so that minimizes some of the increased risk of severe hurricanes.
MJ Sorority has consulted extensively with industry experts to create a list of recommendations for your chapters as they consider updating or replacing their chapter house roofs. At a minimum, we recommend that all of your chapter houses do an intake on the age and condition of their roof, which many roofing companies will do free of charge!
When it comes to fortifying your existing roof or installing a new one, MJ Sorority recommends the following:
- Stronger Edges: strengthening the edges of your roof can help prevent wind uplift during storms, which can lead to roof edge failure. By reinforcing the edges with hurricane straps (not just for hurricanes!) or other secure attachments, the edges of a roof can withstand far greater wind speeds.
- Sealed Roof Deck: adding a layer of protection against water helps minimize the risk of leaks and water damage during heavy rainfall, snow, and hailstorms. Sealing your roof deck not only strengthens your roof but protects the attic and building more generally from potential water damage caused by storms.
- Better Attachment: improving attachment is the best defense for preventing wind and wind-driven debris from breaking your roof loose from the rest of the structure.
- Impact-Resistant Shingles: investing in stronger shingles provides an additional layer of defense against hail and wind-driven debris impact. Designed to withstand high velocity impacts, these shingles reduce the likelihood of damage and the frequency of repairs.
- Wind and Rain Resistant Attic Vents: upgrading attic vents maintains stable ventilation to the home’s interior, while simultaneously protecting against water and debris that may damage your roof and attic during a storm.
- Impact Protection for Windows and Doors: the use of impact resistant materials to reinforce windows and doors mitigates the risk of them breaking or coming lose, leaving your property vulnerable to water and debris. An additional benefit to impact protection is security, making it nearly impossible to break through a window, even when the top layers of glass have shattered.
Given the heightened risk of volatile weather, it is imperative that organizations do an intake and analysis of the health of chapter house roofs. Taking proactive measures to update and fortify roofs and bridging the gap between building codes and insurance requirements can mitigate the risk of roof damage and will maintain the safety and longevity of your properties. Prioritizing the fortification via the recommendations above will not only enhance the overall structural integrity of the properties in question but will also undoubtably contribute to the long-term sustainability of these important spaces for members.
Further Reading:
So, we’re betting at least some of your apps and online accounts have asked, “Do you want to opt into two-factor identification?” And, if you’re like many people, all that texting and code retrieval might seem just a little too much trouble.
Is all that security really necessary? Short answer: YES. And it doesn’t have to be hard.
Why should you use two factor identification?
Cyber attacks, personal data leaks, and phishing scams are becoming more common as hackers get more sophisticated and as we conduct more of our personal and financial transactions on apps and online. Scary factoid: the FBI’s Internet Crime Complaint Center reported that people lose $57 million in phishing and smishing schemes each year.1
Two-factor identification (2FA) provides an extra layer of protection to help safeguard your personal data and your dollars when you are accessing websites and apps.
What exactly is two-factor identification?
Also referred to as “two-step authentication,” “two-step verification” or “multi-factor authentication,” 2FA is an electronic security protocol that prevents you from accessing a website or an app until you validate your identity with two or more pieces of proof. This helps ensure that unauthorized users can’t pretend to be you.
Multi-factor identification “secures your logins from attackers exploiting weak, stolen, or leaked credentials,” says Laura Bennett, Senior Vice President, e-Consumer North America for BlinkSM by Chubb®.
How do you enable 2FA protection?
Many widely-used internet service providers (e.g. Google, Apple, Amazon) and social media platforms (e.g. TikTok, Snapchat, Facebook/Instagram), as well as financial sites, productivity, and personal apps (e.g. Paypal, Slack, Fitbit) have 2FA capability.
- A helpful website that lists sites currently offering multi-factor identification can be found here: 2FA Directory.
- Enabling 2FA is typically done through your user account and/or security tab. Instructions vary, so check with the individual sites or apps for specifics.
- There are a number of authentication apps that consolidate and streamline your 2FA efforts. In other words, the app automatically authenticates you and eliminates the code sending step. The advantages of using these are that they typically work even when you don’t have access to cell service, and they are considered more secure than text messages. Some of the most popular apps are Authy, Google Authenticator, Duo, and Microsoft Authenticator.
We do not endorse any particular vendor or brand of 2FA, but consumers should take time to research options along with the benefits of utilizing 2FA for their circumstances.
Is two-factor identification foolproof?
Currently, 2FA apps are the most secure user authentication methods. However, it is important to always practice good cyber hygiene habits:
- “Leverage alerts on all accounts (especially financial) to warn you of suspicious activity,” Bennett advises.
- Use a strong and unique username and password and never save passwords in your web browser.
- Keep your computer’s operating system up to date. This is to ensure you have the latest security features in place.
- Be wary of emails, texts, or attachments from unfamiliar or suspicious-looking senders especially those that ask for personal data.
- Avoid using open wi-fi networks, which are easily hacked.
We do not endorse any particular vendor or brand of 2FA, but consumers should take time to research options along with the benefits of utilizing 2FA for their circumstances.
Source: Chubb, the cyber insurance provider for MJ Sorority
Note: We have recently had several check fraud claims. We asked our partners at The National Bank of Indianapolis to write the following article to help you protect yourself from check fraud. See also our previous article on the subject.
Financial losses due to fraud are increasing every year. According to the FCC, losses due to fraud were up by more than 30% in 2022 compared to 2021. Nonprofit organizations tend to be particularly at risk due to 990s and other information useful to fraudsters being publicly available.
Particularly alarming is the rise in check fraud. FinCEN released a recent report indicating that check fraud occurrences reported by banks increased to 680,000 in 2022 from 350,000 in 2021.
It is often recommended that we minimize the use of paper checks as much as possible. Electronic credit card and ACH payments (with verified and secure payment portals), while not perfect, are much more secure. Credit cards also tend to have the most generous reimbursement terms if fraud does occur.
While this is sound advice, it is sometimes simply unavoidable to use paper checks as a form of payment. Here is some general information and steps you can take to help protect your organization:
Check Processing and Check Fraud Trends:
Today, the processing of checks by banks is nearly all automated. Gone are the days of banks examining individual checks and matching to signature cards. Anyone with your account and routing number can easily create fake checks. On the bright side, bank processing software has become more sophisticated in detecting anomalies in check style and out of sequence check numbers.
In response, the criminals are now trending back to intercepting real checks and changing the payee information. This way, an altered check can be paid, and possibly go unnoticed for a much longer period of time. Unless cancelled checks are examined closely, they can reconcile correctly, and not be noticed until the intended payee calls. Depending on the payee’s accounts receivable systems, this is sometimes months later.
How to Protect Your Organization:
1. Positive Pay: Most banks offer this service for a fee, and there is no better defense against check fraud. It works by matching all checks that are drawn on your account to a file you send to the bank at the time you issue them. If any information does not match, you are notified and have the opportunity to deny payment.
Some banks have different versions of Positive Pay, so make sure that your service is verifying the payee name as well as the other information on the check.
There is a similar “ACH Debit Filter” product which protects against unauthorized ACH debits which is also highly recommended.
Should you reject this optional risk management too, it will be incumbent upon you to manage your financial transactions in a more timely and more thorough manner.
2. Outsourced Payables Processing: Many organizations hire third parties to manage the processing of payables. The processors generally prefer to send payments via ACH, and only use paper checks when necessary. Usually, they will debit your account once and pull the funds into their bank account, and then make payments to your vendors from there. They should all have Positive Pay, but sometimes fraud still occurs. It is important to review their contracts and disclosures carefully to understand how fraud is handled and who is liable. Some of them have time limits after which they will not reimburse for fraud losses.
3. Reconcile and review account activity frequently: Identifying fraud as soon as possible is critical as the chances of recovering the funds diminish quickly with time. If a fraudulent check is reported within 24 hours, it can usually be returned before funds ever leave your account. Organizations that choose to not incur the expense of Positive Pay must be particularly vigilant.
4. Report fraud to your bank no later than 30 days from the incident. Regulation CC (the Federal regulation governing check processing and liability) requires the bank of first deposit to conduct specific actions if it is notified within 30 days. After that, the opportunity for recourse is greatly reduced.
5. Secure Check Stock: Protecting both unused check stock, and outgoing checks is another critical aspect of protection. Many of the intercepted checks are stolen from the mail. Unsecured mailboxes should be avoided.
What To Do if Fraud Occurs:
1. Notify Your Bank Immediately: The sooner the bank is notified the better the chances of recovering the funds. Your bank should also guide you through the process and advise on next steps.
2. File a Police Report: In addition to getting the police involved, this is a very important step to document the occurrence for potential insurance claims, and disputes down the road with intended payees.
3. Contact the Postal Inspector’s Office – If a check was stolen in the mail, be sure to file a report with this office. They also tend to be more proactive about pursuing fraudsters than the police.
4. Contact MJ Sorority to alert them to the incident and determine any additional action that needs to be taken.
In Summary:
As the threat of check fraud continues to evolve, we all must remain vigilant and proactive in educating ourselves and our employees . Staying informed about emerging trends, leveraging advanced banking technologies, and adopting best practices will help fortify our defenses. It is important to have a good relationship with a knowledgeable and responsive banking partner who can help develop and continuously improve your defenses against losses due to fraud.
We have seen a recent uptick in phishing scams among MJ Sorority clients. In today’s digital age, the threat of phishing is more prevalent than ever before. Did you know that over 90% of successful hacks and data breaches start with phishing scams? It’s a sobering statistic that underscores the importance of staying vigilant against this pervasive threat.
But what exactly is phishing? Simply put, it’s the process of attempting to acquire sensitive information, such as usernames, passwords, and credit card or bank account details, by masquerading as a trustworthy entity. Phishers often use bulk emails that try to evade spam filters, claiming to be from popular social websites, banks, auction sites, or IT administrators. It’s a form of criminally fraudulent social engineering that preys on unsuspecting individuals.
Understanding the Techniques
Phishing techniques have evolved over the years, becoming increasingly sophisticated and diverse. From traditional email and spam campaigns to more targeted approaches like spear phishing and session hijacking, cybercriminals employ a wide array of tactics to deceive their victims. They manipulate links, inject malicious content, and even resort to voice calls and SMS messages in their quest to obtain personal information.
Stay Vigilant
So, how can you protect yourself against phishing attacks? Awareness is key. Familiarize yourself with the common techniques used by cybercriminals, and adopt anti-phishing strategies to safeguard your information. Be cautious when clicking on links or downloading attachments from unknown sources, and always verify the authenticity of requests for personal or financial information.
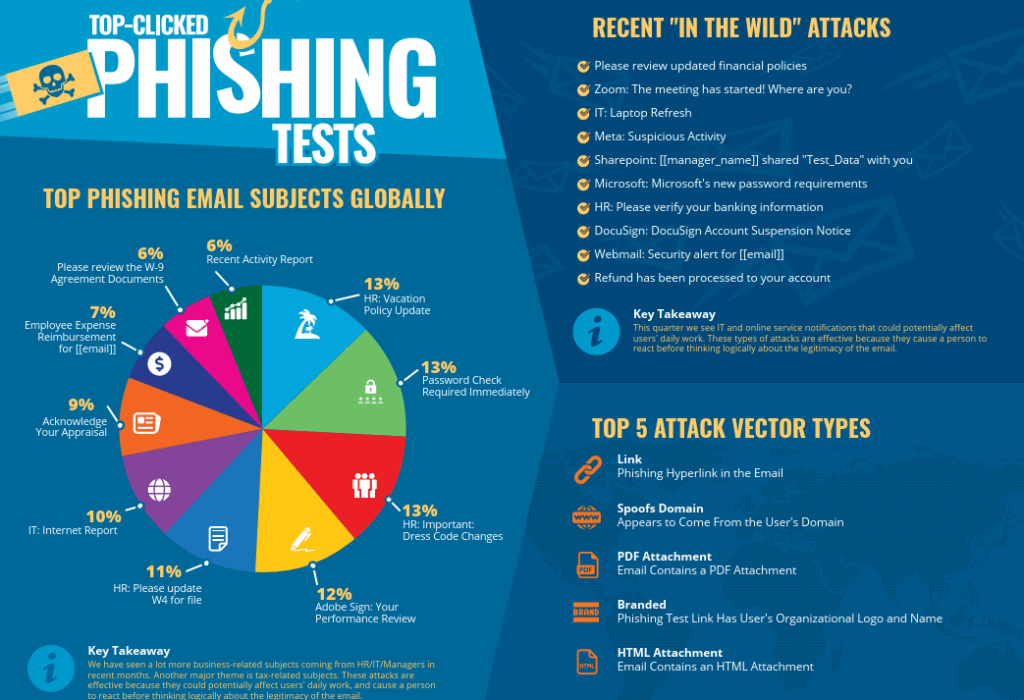
At MJ, we utilize KnowBe4, a firm that provides security awareness training to members of your organization. Each quarter, they produce an infographic with the top types of phishing attacks, as excerpted above. For the full infographic and associated data, click here. KnowBe4 also offers a free phishing security test that you can utilize to see if your employees are susceptible to phishing attacks – learn more here.
The past year saw a surge in severe convective storms, particularly hailstorms, causing billions in insured losses across the US. This trend is likely to continue in 2024 and beyond, impacting insurance premiums and available coverages, especially for properties like sorority chapter houses.

The graphic above shows the increase in the number of hail storms and the severity of the damage associated with them over the last twenty years. To zoom in and read the entire report, which we found very informative, click here.
These storms, packing powerful winds, hail, and heavy rain, pose a significant threat. In 2024 and beyond, the risk of severe convective storms looms large, driven by a combination of factors such as warmer atmospheric temperatures, higher moisture content, and shifting wind patterns. These storms can unleash destructive winds, large hailstones, torrential rainfall, and even tornadoes, causing extensive damage to buildings and infrastructure in their path.
Sorority chapter houses, often located in areas prone to severe weather, often face heightened exposure to convective storms. Their typically large, historic structures may be more susceptible to damage from high winds and hail, leading to costly repairs or even total reconstruction. Furthermore, the social nature of sorority houses means that they are frequently occupied, putting members at risk during severe weather events.
Insurance companies take these risks into account when setting premiums for property coverage. As the frequency and severity of convective storms increase, insurers may adjust their pricing models to reflect the heightened risk. Other options for insurers in this new environment include: stricter requirements for risk mitigation measures, such as installing impact-resistant roofing materials or reinforcing windows and doors against high winds.
In response to these challenges, sorority chapters must prioritize proactive risk management strategies. These strategies include the following recommendations and resources:
- Thorough property inspections semi-annually. We recommend our Chapter House Self-Inspection form, which guides you through common concerns to look out for.
- Implementing preventive measures to strengthen the building’s resilience against severe weather
- Having an emergency plan and educating members accordingly
By staying informed and taking proactive steps, sorority houses can weather the storm – both literally and figuratively.
Water damage poses a significant threat to sorority chapter houses, often resulting in costly repairs, business interruptions, and reputation damage. In this resource, we share tips and strategies to effectively prevent water damage and safeguard the integrity of sorority chapter houses. For a shorter, visual resource, click here.
Prevent sewer and wastewater system backups
- Pay special attention during times of heavy rain, as sewers can get overwhelmed, becoming blocked, resulting in a back-up causing polluted water to flow directly into the chapter house.
- Have an emergency plan for shutting down inflow systems.
- Install water detection sensors behind these systems.
Prevent Water Heater Issues
- The typical lifespan of a water heater is 8-10 years so have a replacement program in place.
- Routinely look for signs of rust and corrosion.
- Keep water pressure no higher than 80 psi / 552 kFa
- Install a catch pan (drip pan) under the heater to catch small leaks
- Install water detection sensors behind these systems
Keep HVAC Equipment Working Well
- Look for clogged drains, frozen evaporator coils, and pipes not properly connected, which are primary culprits of HVAC leaks.
- Change filters regularly to keep unit from overworking.
- Make sure condensation drain line is clear on a monthly basis.
- Install water detection sensors especially in unheated spaces that have piping concealed.
Pay Attention to the Plumbing
Domestic plumbing is the primary culprit of water damage. Most claims involve leaking pipes caused by corrosion, pipe burst, or failure. Failure to prevent and control corrosion is the root cause. Unfortunately, most corrosion is internal and is not easily identified. Galvanic corrosion is one of the most common types of corrosion.
- Look for visible corrosion
- Listen and watch for rattling, shock or vibration when water is turned on or off, which might indicate a piping support issue
- Replace piping that is over forty years old
- Look for blue or green staining on sinks or taps, which indicates high concentrations of carbon dioxide.
- Check for acidic water and treat hard water.
Plumbing in Bathrooms and Kitchens
- Keep an eye on toilets, sinks, and other common bathroom fixtures, especially in multi-story houses with stacked plumbing. Make sure resident members bring all leaks to the attention of either the House Director or the Collegiate House Officer.
- Inspect all plumbing hoses periodically, especially their coupling connections.
- Replace hoses that show signs of imminent failure. Most manufacturers recommend hoses to be replaced every 3-5 years.
- Install water detection sensors under sinks, dishwashers, ice makers, laundry washing machines and other appliances.
To Keep Roofs from Leaking
- Conduct routine inspection and maintenance
- Repair all conditions that affect the viability of the roof
- Unclog roof drains and gutters
- Safely remove excess snow and ice from the roof
Water is invasive and there are some things even the very best insurance coverage can’t replace. When it comes to water, the best protection is risk prevention and it’s more critical than ever. 55% of property claims in the MJ Sorority program are due to water-related issues, from burst water pipes to sewer and drain backups. Given the age of many of our properties, these occurrences are not unexpected. For more information on how and why to install leak protection systems, including a 5% premium credit, please refer to our paper on leak protection.
Therefore, proactive risk prevention measures are paramount, especially in the face of these challenges. Adopting technological solutions can greatly enhance a chapter house’s water protection system. Here are four key types of technology solutions that can be employed:
- Smart Leak Detectors / Sensors: These devices serve as the frontline defense against water damage by detecting moisture and leaks throughout the property. Strategically placed sensors can promptly alert housing corporations and property managers via mobile notifications upon detecting any signs of leakage.
- Smart Water Monitors: By monitoring water flow within the chapter house, these devices can identify abnormal patterns indicative of leaks. They can be integrated with plumbing systems to provide real-time alerts in case of leaks, and some models offer insights into water usage for efficient conservation.
- Smart Water Shut-Off Valves: These valves provide a proactive approach to mitigating water damage by automatically shutting off the water supply in the event of a detected leak. Remote activation capabilities enable housing corporation personnel and property managers to control the valve even when away from the property.
- Freeze Sensors: Designed to prevent frozen pipes, these sensors detect temperature drops within the property and trigger alerts or notifications when temperatures reach critical levels, typically around 45°F (7°C).
In addition to technological solutions, implementing a comprehensive preventative maintenance program is essential. Regular inspections by professionals can identify vulnerable areas and minimize downtime, enhancing overall reliability.
Given the persistent challenges posed by water damage, the MJ Sorority Program strongly recommends the adoption of these advanced technologies. Because of the potential damage caused by water leaks in the chapter house, we have negotiated with the property insurance carrier to offer our clients who install leak detection systems with the applicable monitoring functionality a five percent credit to their property premium.
Consider using one of these best-in-class leak detection technology companies:
Other leak detection companies that we have researched include the following:
Failure to address water damage proactively may lead to increased insurance deductibles and further financial strain. As such, property managers are urged to explore and implement these solutions to safeguard their chapter houses effectively.
Help us welcome our new Director of Risk Management Education and learn more about Kit Moorman. Learn more and read our press release.
When winter weather strikes, drivers face out-of-the-ordinary challenges when they get behind the wheel. Snow, slush or icy roads are involved in nearly one in four weather-related vehicle crashes. These conditions can make it harder for drivers to see, slow down and stop – all factors that can increase the chances of an accident.
If you must travel during winter weather, preparing your car in advance, knowing the forecast and driving based on road conditions are three key ways to help you drive more safely. Following are some winter driving safety tips to help you prepare for the elements – before you face them – on the road.
Preparing Your Vehicle
As temperatures start to drop, it’s time to make sure your car is stocked with a winter driving survival kit, including an ice scraper, a snow shovel and sand or road salt. This way, you’ll be prepared if winter weather arrives while you’re away from home. It’s also a good time to check your tires to determine whether it’s time to replace them or whether you need snow tires.
A few habits to adopt regularly during the winter months can also help prepare you for a wintry drive. Keep your windshield wipers in good condition and your windshield fluid reservoir filled so you can clear snow and ice from your windshield. Make it a practice to keep your gas tank full so you can run your engine and stay warm if you get stuck or stranded.
Keeping your gas tank full in extended cold weather can also help minimize the amount of water vapor in your tank, which can freeze when temperatures drop. In addition to keeping the tank full, consider keeping your vehicle in a garage and using fuel additives such as dry gas to help eliminate water vapor that could freeze in your gas lines. You should also either drive or run your car in a well-ventilated area at least every few days to help avoid a dead battery, another cold weather concern.
Watching the Weather
If you plan to travel when inclement weather looms, monitor road and weather conditions by checking local news stations or Internet traffic and weather sites. You can sign up for weather alerts to receive text messages and optional alerts for your area. Do not check your phone while driving and avoid all unnecessary distractions when you’re behind the wheel.
Driving for Winter Conditions
Before you leave the driveway or parking lot, take time to clear snow and ice off your car, including your windows, mirrors, lights, reflectors, hood, roof and trunk. Drive with your headlights on and be sure to keep them clean to improve visibility. Use caution when snow banks limit your view of oncoming traffic.
As you get on the road, remember that speed limits are meant for dry roads, not roads covered in snow and ice. You should reduce your speed and increase your following distance as road conditions and visibility worsen. Avoid using cruise control in snowy or icy conditions – you want to have as much control over your car as possible. Be cautious on bridges and overpasses as they are commonly the first areas to become icy. Avoid passing snow plows and sand trucks because the drivers may have limited visibility and the road in front of them could be worse than the road behind.
Breaking Down or Getting Stuck
If you are unexpectedly caught in a snowstorm and are stranded or get stuck in snow, if your car is safely out of harm’s way, stay in your car and wait for help. You can run the car heater to stay warm for 10 minutes every hour, but first, make sure your exhaust pipe is clear of snow. There is a danger of carbon monoxide poisoning if snow blocks the pipe and enables the deadly gas to build up in your car. Open your window slightly to help prevent any buildup.
Remember, driving in winter weather can be challenging, even for experienced drivers. Slowing down, allowing increased time to come to a stop, wearing your seatbelt, devoting your full attention to the road and being aware of changing conditions can help you drive more safely. If your travel route takes you into remote areas with limited cell phone coverage, consider informing a third party of your travel plans and share with them your route and when you plan to arrive. This way, if you are overdue, first responders will know where to start looking. If you’re unsure whether it is safe to drive, consider waiting until the roads improve.
Source:
https://www.travelers.com/resources/auto/safe-driving/winter-driving-safety-tips
We have recently had several claims involving fraudulent checks. Sororities aren’t the only victims. In an alert sent out in February, the Financial Crimes Enforcement Network, also known as FinCEN, reported that, “Despite the declining use of checks in the United States, criminals have been increasingly targeting the U.S. Mail since the COVID-19 pandemic to commit check fraud.” Criminals are becoming increasingly sophisticated in their methods, making it crucial for organizations to stay vigilant. These fraudulent activities encompass a range of tactics, including counterfeit checks, altered payee information, and even identity theft to gain access to legitimate bank accounts. As a result, it is imperative for chapter and house corporation officers and volunteers to be aware of these risks and adopt strategies to mitigate the threat of check fraud. We recommend the following strategies:
- Secure your checks: Store your checkbook, blank checks, and deposit slips in a secure and locked location. Limit access to these items to only trusted individuals. Consider using a secure check stock with built-in security features like watermarks or microprinting.
- Try and limit exposure by reducing check use. Transitioning to electronic checks and digital payment methods reduce the risk associated with paper checks.
- Make sure you’re following internal safety measures. Chubb Insurance, the insurance company who writes your Crime Insurance Coverage, has some basic risk management rules and guidelines for the entities under your organization’s national insurance policy. These conditions are referred to as “required conditions” and list out specific requirements in the financial management to ensure that there is dual control of the financial transactions at all times. These measures help prevent check fraud, as well as other financial crimes. Read more here.
- Consider Positive Pay: Enroll in Positive Pay services offered by your bank. This service helps detect discrepancies by matching the checks presented for payment with a list of authorized checks you’ve issued. Positive pay procedures set permissions in a checking account, so the company gets confirmation before a check or ACH Debit against your company is processed. ACH: ACH stands for Automated Clearing House and is a network that transactions pass through in the United States. The network exists to manage the transfers and organize them. ACH debit is the transaction executed through the Automated Clearing House Network.
- Train employees and volunteers: Educate employees and volunteers about the risks of check fraud and teach them how to recognize signs of suspicious activity. Ensure they understand the importance of safeguarding sensitive financial information.
- Stay informed: Keep yourself informed about the latest trends in check fraud and adapt your prevention strategies accordingly. Criminals continually evolve their tactics, so staying up-to-date is essential. Count on MJ Sorority to continually monitor the trends and communicate new strategies to you.





